DDOS Attack on X What Really Happened?
When tech billionaire Elon Musk flagged a “massive DDOS attack” on X, the disruption wasn’t just a minor inconvenience; it was a significant event that overshadowed the airing of his highly anticipated interview with former President Donald Trump. This incident has sparked intense discussions about the implications of such cyber attacks on platforms, their users, and the broader tech landscape. In this article, we’ll dive deep into what a DDOS attack is, how it impacted X, and what it means for the future of digital security.
The DDOS attack on X that disrupted Elon Musk’s interview with Donald Trump highlights the vulnerabilities that major tech platforms face. While the immediate impact was significant, the broader implications for digital security are even more profound. As technology evolves, so too must our approaches to protecting against cyber threats.
The incident raises important questions about the future of cybersecurity and the measures needed to safeguard digital platforms. As we continue to rely more on technology for both personal and professional purposes, understanding and addressing these threats becomes increasingly crucial.
What is a DDOS Attack?
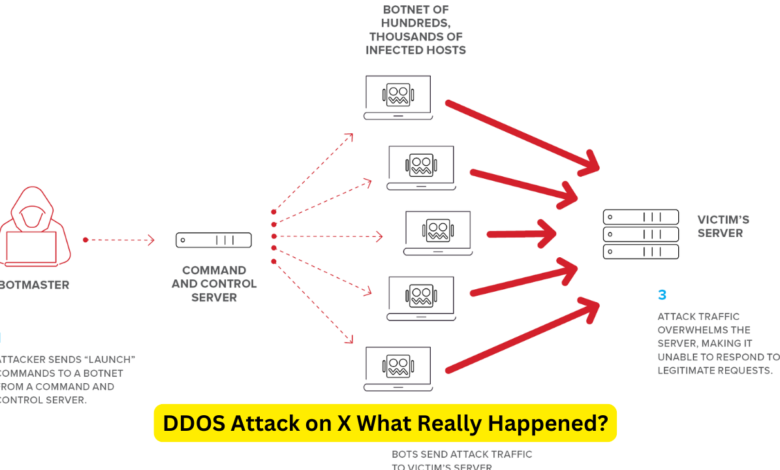
Before we dive into the specifics of the incident, it’s essential to understand what a DDOS attack entails. DDOS stands for Distributed Denial of Service. Essentially, it is a malicious attempt to disrupt the normal functioning of a targeted server, service, or network by overwhelming it with a flood of internet traffic. This flood of traffic originates from multiple sources, making it difficult to mitigate the attack.
How DDOS Attacks Work
A DDOS attack works by using a network of compromised computers, often referred to as a botnet, to send an excessive amount of requests to a server. This massive influx of traffic can exhaust the server’s resources, leading to performance degradation or complete shutdown. The goal is to make the service or site unavailable to its intended users.
The DDOS Attack on X: What Happened?
Elon Musk’s revelation about the DDOS attack on X drew significant attention. According to reports, the attack occurred during a critical moment—the airing of Musk’s interview with Donald Trump. The timing was particularly damaging, as the interview was highly anticipated and attracted substantial viewership.
Immediate Impact on the Interview
The DDOS attack caused severe disruptions, preventing many viewers from accessing the stream. This interruption not only frustrated viewers but also raised questions about the vulnerability of major tech platforms to such attacks. The incident underscored how crucial it is for platforms to have robust security measures in place.
Broader Implications for X
For X, the attack wasn’t just a technical challenge; it was a public relations issue. Users and critics alike began questioning the platform’s ability to handle high-traffic events securely. The attack also highlighted the potential risks associated with live-streaming major events, where a single security breach can have far-reaching consequences.
Why Are DDOS Attacks So Disruptive?
The disruption caused by DDOS attacks goes beyond mere inconvenience. Here’s why they are so problematic:
- Overwhelming Resources: By flooding a server with traffic, DDOS attacks deplete its resources, making it unable to handle legitimate requests.
- Costly Mitigation: Defending against a DDOS attack can be expensive. Companies often need to invest in additional security measures and resources to manage and mitigate the attack.
- Reputational Damage: Beyond technical and financial impacts, DDOS attacks can harm a company’s reputation. For platforms like X, where user trust is paramount, any disruption can lead to a loss of credibility.
How Can Platforms Defend Against DDOS Attacks?
Given the potential for DDOS attacks to cause significant disruptions, it’s crucial for platforms to implement effective defenses. Here are some strategies:
1. Traffic Analysis and Filtering
Advanced traffic analysis tools can help identify and filter out malicious traffic before it reaches the server. This involves monitoring traffic patterns and blocking suspicious activities.
2. Scalable Infrastructure
Platforms can leverage scalable cloud infrastructure to handle sudden spikes in traffic. Cloud services often come with built-in DDOS protection and can dynamically adjust resources to manage increased load.
3. Rate Limiting
Rate limiting involves restricting the number of requests a user can make in a given time frame. This helps prevent any single user or bot from overwhelming the server with requests.
4. Redundancy and Failover Systems
Implementing redundancy and failover systems ensures that if one server is under attack, traffic can be redirected to another server. This helps maintain service availability even during an attack.
What Does This Mean for the Future?
The massive DDOS attack on X serves as a wake-up call for tech companies and platforms worldwide. As digital interactions and live streaming become increasingly common, the risk of such attacks is likely to grow. It’s essential for companies to stay ahead of these threats by investing in advanced security technologies and strategies.
The Role of Cybersecurity in Tech Innovation
As technology continues to advance, so do the tactics used by cybercriminals. Cybersecurity is not just about protecting data but ensuring the seamless operation of services that billions of people rely on. Tech companies must prioritize security alongside innovation to build trust and ensure a stable digital environment.
Conclusion
The DDOS attack on X that disrupted Elon Musk’s interview with Donald Trump highlights the vulnerabilities that major tech platforms face. While the immediate impact was significant, the broader implications for digital security are even more profound. As technology evolves, so too must our approaches to protecting against cyber threats.
The incident raises important questions about the future of cybersecurity and the measures needed to safeguard digital platforms. As we continue to rely more on technology for both personal and professional purposes, understanding and addressing these threats becomes increasingly crucial.
What are your thoughts on the impact of DDOS attacks on major tech platforms? Do you think current security measures are sufficient, or is there more that needs to be done? Share your thoughts in the comments below!
For additional resources on cybersecurity and how to protect your digital presence, check out these links:





2 Comments